Prevent Phishing
Doubting the legitimacy of a web page, or an email? Call the Helpdesk! +31 20 592 2200 or mail security@nikhef.nl
Aim: protect yourself and Nikhef by verifying you're talking to the right service.
Target audience: everyone with a Nikhef account.
Are you talking to the real Nikhef? Don't take the bait!
Phishing email is often the first step to penetrate an organization, such as Nikhef. We need your help and vigilance to keep our systems and your privacy and data secure.
Following that mail, or even already in the first mail, the attacker will send you 'malware', aiming to compromise you and your data. Claims about 'security of your account', or about a suspicious bank transaction, and then urging you to click on a link, is often the lure to get to you let your guard down and click. At times they may even just send you a file with instructions: luring you to actually help commit the fraud.
But attacks can come also through social media, like Facebook, WhatsApp, SMS, or links on public forums. Fraudsters are specifically targeting Nikhef - and lure you by mentioning names of real colleagues!
- Check the URL in your web browser, and, if in any doubt, retype the URL by hand and check the owner of the web site
-
All Nikhef web sites where you have to enter your username and passphrase have a trusted certificate that identifies Nikhef
-
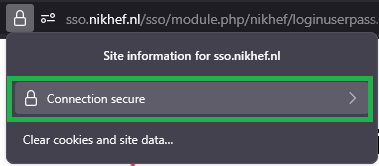
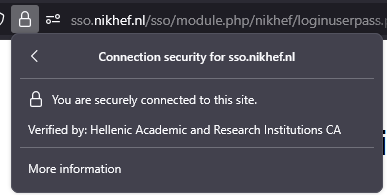
Check for Organisation validation showing "Nikhef", by clicking on the padlock in the address bar to check that it was issued to "Nikhef" by the "Hellenic Academic and Research Institutions CA":
Recognize attacks
The following are strong indicators for dangerous phishing:
- urgency ("you must react within 2 days to prevent your account from being removed")
- authority ("Copyright © 2023 nikhef.nl security management")
- mimicry ("your colleague David asked me to send you this ...")
- curiosity ("we spent a lot of time on the new debit card design, and are proud of the result ...")
- being asked to log in where you would not normally expect it (to "open a secure document" or so)
Your Nikhef credentials are very powerful indeed
Can you help us protect them?
- look at veiliginternetten.nl (in Dutch)
- Take the test! The UK NCSC has a nice quiz to see if you can recognize advanced phishing, or
- print the poster, or
- watch this creative video to see what can happen
Can you recognise phishing URLs?
Can you see which URL is taking you to David's Nikhef Webmail?
https://webmail.nıkhef.nl/SOGo/so/davidg/Mail
https://webmail.nikhef.nl/SOGo/so/davidg/Mail
https://webmail.nikhef.nl:SOGo/so/davidg@nikhef.web/Mail
Actually, number 2 is the only proper one! - no. 1 is wrong, since the "i" is not a real "i", but an "ı" that looks very similar, but comes from the Turkish alphabet (it lacks a dot ...). Domain names can be internationalized and contain non-Latin characters - no. 3 is wrong, since the domain name part only starts after the at ("@") sign! Everything before the "@" is considered a "username" and "password" (both of which are obviously fake in this case. You will be sent to "nikhef.web", which is not ours! There are very many top-level domains nowadays, most of which are homes of fraudsters. OK, except for ".cern" ...
Call us!
If you have any questions or doubts, just contact us. You can send mail to security@nikhef.nl or visit www.nikhef.nl/security to find our contact details. You can also call 2200 during office hours.
Thanks to our sources: the NL National Cyber Security Centre (NCSC.nl) and the UK Centre for the Protection of National Infrastructure.